The SEAGLASS Project
Currently, modern mobile phones are exposed to attacks from rogue cellular transmitters called IMSI (International Mobile Subscriber Identity) Catchers, surveillance devices that can easily and precisely locate cell phones, eavesdrop on conversations and even send spam.
The SEAGLASS project, a group from the University of Washington security researchers, has developed a system to detect anomalies in the cellular landscape that able to indicate where and when these surveillance devices are being used. This system is described in a paper that has been published in June 2017.
In 2017, in order to catch these IMSI-catchers in the act, SEAGLASS used sensors built from off-the-shelf parts that can be installed in vehicles, ideally ones that drive long hours and through many parts of a city. The sensors picked up signals broadcast from the existing cell tower network, remaining legitimately constant. Then, the SEAGLASS team aggregated that data over time in to create a baseline map of “normal” or standard cell tower behavior.
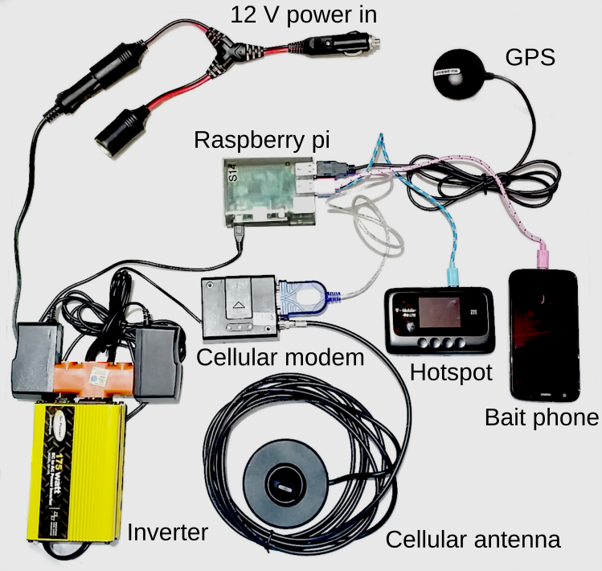
Figure 1 Sensor setup built by Seaglass before 2017
Methodolody
Establishing local allies or LCO’s (Local Coordinating Organizations) across Latin America, we had put into practice what the project SEAGLASS team from the University of Washington tested before within cities such as Seattle and Milwaukee.
Within approximately 90 days, the local allied and other organizations collected data scanning the city, following these steps:
- Get a Smartphone (Any Android phone should work).
- Get a feature phone in order to use it as an antenna (at the moment, we used any Osmocom compatible phone like the Moto C139).
- Buy or build a Serial – USB cable to connect the smartphone with the feature phone.
- Download and configure app on the smartphone.
- Start a data collection and analysis server.
- Review, validate, and process analysis results.
Recently, the SEAGLASS team proposed and launched a new sensor architecture that resulted easier to only to build and operate but also cheaper, based on one Android smartphone with a specific app installed. A feature phone compatible with the OsmocomBB project that will be used as a reception antenna, this setup has proven to be effective in the data collection and makes possible to implement the SEAGLASS workflow in a more efficient, more accessible and cheaper way.

Figure 2 Current sensor setup built by Seaglass
How does it work?
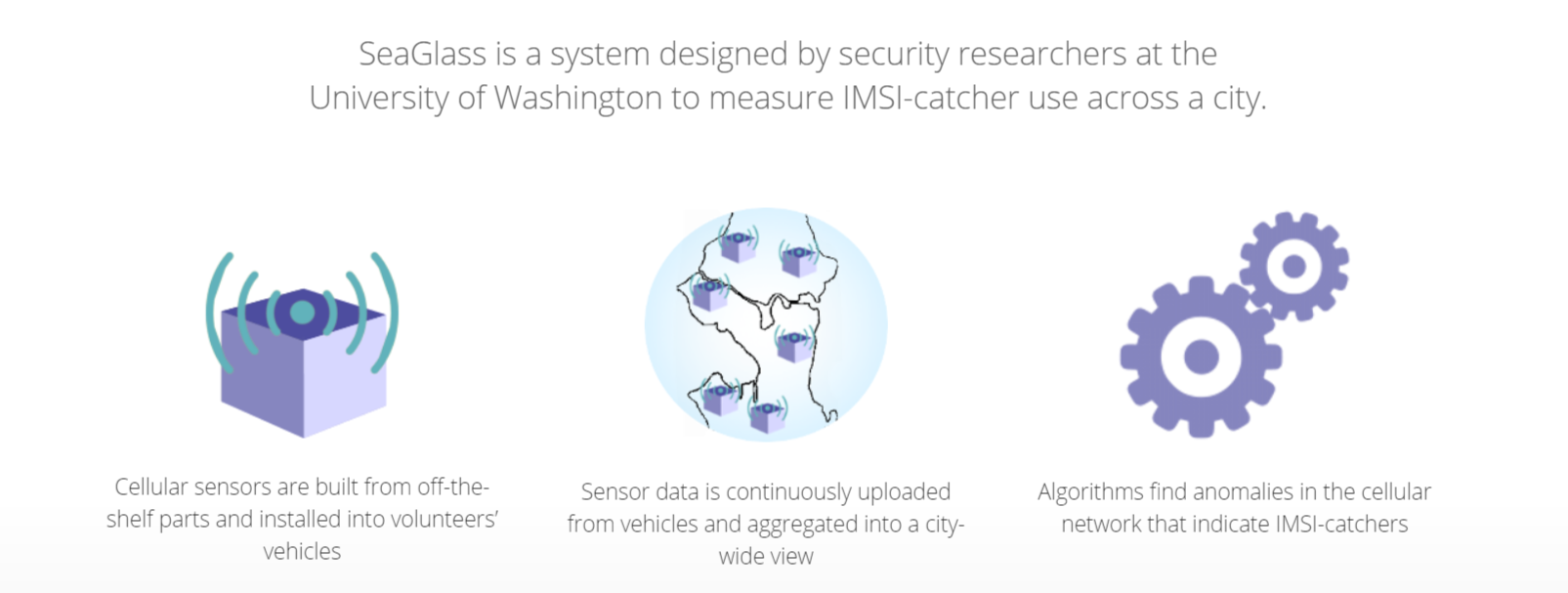
By modeling the typical behavior of each cell tower over time, SEAGLASS can pick out aberrations that indicate the presence of cell-site simulators.
For IMSI-catchers to function as surveillance devices and to operate covertly, they must give off certain signature anomalies that can be detected. The team behind SEAGLASS project has proposed some detection methods that use the data collected to automatically flag these anomalies on several ways.
Detection methods
1. Portability
This is when we see that a specific cell tower is physically moving among different locations.
2.Temporality
This is when we see that a specific cell tower is working only in a particular time window.
3. Issuance of suspicious configurations
This is when we see a specific cell tower configured with suspicious frequencies or other settings not observed in the rest of the network.
4. Inconsistencies in geographic data
This is when we see that a specific cell tower is configured differently from the other towers from the same carrier and/or geographic zone.
5. Suspicious interactions with mobile phones
This is when we see that a specific cell tower is instructing a phone connected to it to not connect to any other cell tower, to degrade its protocol from 3G/4G to 2G, or to communicate in an unusual frequency among other strange commands.
For more information please visit https://seaglass.cs.washington.edu/
FADe project is an initiative of South Lighthouse with the support of the Open Technology Fund.
![]()
![]()
This website is available under a Creative Commons Attribution 4.0 International (CC BY 4.0) License creativecommons.org