Project Description
The Fake Antenna Detection Project is aimed to develop the strategy proposed by the SEAGLASS project at the University of Washington and the Crocodile Hunter project developed by the Electronic Frontier Foundation (EFF) to detect the use of IMSI-Catchers with a standardized methodology within Latin America to develop its promotion, technical tools, and data obtained with local allies. Our main objectives are:
- Apply, document, and test methodological variations using technical tools.
- Share the outcome results with local free speech organizations, researchers, academia and/or independent media outlets.
The Fake Antenna Detection Project has been managed by South Lighthouse, an organization aimed at designing, monitoring, controlling, consulting, and training projects oriented to the research and development of technologies at the service of worldwide human rights, security, and privacy.
a. Quick reminder 1: What is an IMEI?
The IMEI (International Mobile Station Equipment Identity) is a 15- or 17-digit code that has one principal purpose: To identify mobile devices physically and also in the phone network. Their secondary objective is to prevent theft. If a mobile device can be universally recognized, a thief cannot change the SIM card on the phone and expect to keep the phone. IMEI numbers are hard-coded into device hardware, making it nearly impossible to change them without somehow damaging the device.
In most mobile communications devices, the IMEI appears on the display when the user enters *#06# (star-pound-zero-six-pound) into the phone keypad. The IMEI code may also be printed inside the battery compartment.
Quick reminder 2: What is an IMSI and an IMSI Catcher?
The IMSI (International Mobile Subscriber Identity) is a code that comes inside your SIM card, and that can be tied to you by your phone company or anyone that has been surveilled you for some time, is equivalent to the IMEI code for your phone line. An IMSI Catcher could be defined as a device that pretends to be a cell tower in order to trick your phone into thinking that it is a regular one and connecting to it, giving the IMSI Catcher all the information related to your phone and its communications. An IMSI Catcher can be used to collect IMSI codes from a particular area or to deny service to cell phone users.
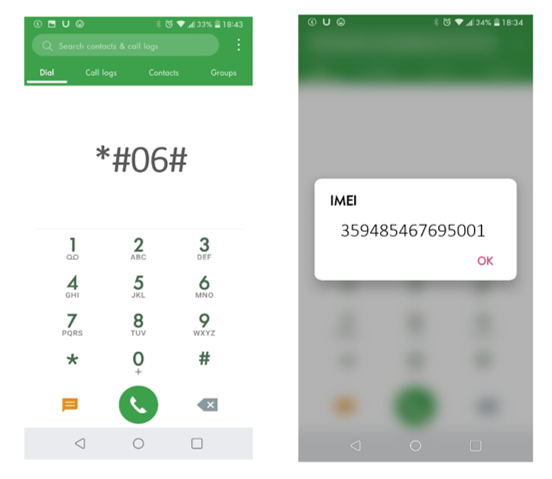
Figure 1. IMEI International Mobile Station Equipment Identity, or MEID Mobile Equipment Identifier.
Project Development






TESTING
Building the sensor setup, using it and checking the data is being uploaded to the server in a controlled environment.
DEPLOYING
It consisted of assembling all the pieces that make up each sensor and distribute them in the monitored cities.
TRAINING
Each local allied organization had training sessions about the sensor and app use, how to read the data, and most important, how to interpret the outcomes of the potential results.
COLLECTING
With a time period of around 90 consecutive days.
PROCESSING
Analyzing the collected data during the monitoring stage, looking for anomalies as proposed by the SEAGLASS Project.
LAUNCHING
It took designing a suitable method for the data collected to be easily understood by non-technical audiences and to generate reports by city.

TESTING
Building the sensor setup, using it and checking the data is being uploaded to the server in a controlled environment.

DEPLOYING
It consisted of assembling all the pieces that make up each sensor and distribute them in the monitored cities.

TRAINING
Each local allied organization had training sessions about the sensor and app use, how to read the data, and most important, how to interpret the outcomes of the potential results.

COLLECTING
With a time period of around 90 consecutive days.

PROCESSING
Analyzing the collected data during the monitoring stage, looking for anomalies as proposed by the SEAGLASS Project.

LAUNCHING
It took designing a suitable method for the data collected to be easily understood by non-technical audiences and to generate reports by city.
Considerations for the implementation





RISK ASSESSMENT
Considering that each country/city has their own risk context, so for each one of them was necessary to build a threat model that considers the specific risks the sensor operators can face by participating in the project. It is necessary to take as an initial premise that the sensors used do not carry out any type of signal transmission or interference with the cellular network.
THREAT MODEL
Take in consideration a number of critical aspects such as:
- Is this kind of monitoring illegal or criminalized by local law enforcement? For the case of the monitored jurisdictions, this did not represent any legal local violations.
- Are there common criminality risks in the cities being monitored? Can the sensors be stolen from the operators, even violently?
- What data will be generated, how can it be traced to the operators and how can we anonymize it?
- Could it be insecure for the operators, allied organizations and volunteers to be publicly promoted by the project?
- Could it be insecure for the project to announce the monitoring before or during it?
TRAINING
Adapting the training efforts to each specific context. Some critical aspects are:
- How to read the data?
- How could it be interpreted or not?
- How to discriminate facts from false positives, etc?
LOCAL CONTEXT
Complete and share risk assessment, and then decide if the local allies will be known publicly. It is necessary to take as an initial premise that the sensors used do not carry out any type of signal transmission or interference with the cellular network.
EARLY PROMOTION
Complete and share risk assessment, and then decide if there will be promotion before the data is collected.

RISK ASSESSMENT
Considering that each country/city has their own risk context, so for each one of them was necessary to build a threat model that considers the specific risks the sensor operators can face by participating in the project. It is necessary to take as an initial premise that the sensors used do not carry out any type of signal transmission or interference with the cellular network.

THREAT MODEL
Take in consideration a number of critical aspects such as:
- Is this kind of monitoring illegal or criminalized by local law enforcement? For the case of the monitored jurisdictions, this did not represent any legal local violations.
- Are there common criminality risks in the cities being monitored? Can the sensors be stolen from the operators, even violently?
- What data will be generated, how can it be traced to the operators and how can we anonymize it?
- Could it be insecure for the operators, allied organizations and volunteers to be publicly promoted by the project?
- Could it be insecure for the project to announce the monitoring before or during it?

TRAINING
Adapting the training efforts to each specific context. Some critical aspects are:
- How to read the data?
- How could it be interpreted or not?
- How to discriminate facts from false positives, etc?

LOCAL CONTEXT
Complete and share risk assessment, and then decide if the local allies will be known publicly. It is necessary to take as an initial premise that the sensors used do not carry out any type of signal transmission or interference with the cellular network.

EARLY PROMOTION
Complete and share risk assessment, and then decide if there will be promotion before the data is collected.
FADe project is an initiative of South Lighthouse with the support of the Open Technology Fund.
![]()
![]()
This website is available under a Creative Commons Attribution 4.0 International (CC BY 4.0) License creativecommons.org